- Content Filter (c,e,s-Wall)
- Content Security via content filtering
- All the information in the network has at least two parameters: address (from/to description) and the data itself (content). Each internet security software or appliance should analyze each piece of the information to make the decision - it is safe for you or it should be blocked. Address part of the information is discussed in Firewall and Zones Sections
- In most cases, address part of the information in not enough for making decision about safety. You should mostly receive all the e-mail and have access to the web all over the world. The single criterion of information security is the content (the data itself). Only by analyzing the content it would be possible to solve - Do you want a banner, is a letters infected, is it spam, is a web page potentially unsafe, might your privacy be disturbed. There are many separate applications providing you with that type security, so called content security. Majority of these applications guard you separately, separate programs for ad blocking, separate for spam suppression, separate for privacy and so on.
- All of them process the internet content under their own, separate point of view. It is possible to perform all these tasks simultaneously. All these tasks are operating with the same data parameters, so they could be performed in the single place by the single universal and configurable mechanism. Fortunately, all the information transmitting via the internet is in the text form. Web pages are the text in HTML, e-mails are texts too (file attachments are converted to the text form before transmitting). There is the universal method for text processing (Regular Expressions - RegExp). That method is used in x-Wall content security.
- Using the rules
- To use the Content Filter you do not need to understand all the Content Rule details. You can only turn on/off the rules you need. Web filtering rules could be verified browsing the set of test pages at x-Club. To verify e-mail filtering rules you could write various test e-mails and send it to yourself.
- You have to know that some web elements could be used at the site you visiting for its functionality. Unfortunately, there is no exact way to predetermine which elements are used for site functionality. Some of those functional elements consider as potentially unsafe (see myths and legends).
- Cookies often used for user authorization. Some sites became unusable if the cookies are turned off
- ActiveX is most dangerous element in the web because it contains a code running directly on your computer. Nevertheless, some sites are using them for their functionality. Well-known flashes are ActiveX too.
Security is always the opponent to availability. The best way is to use default filter settings. If you find, that a site does not work, you should start gradually enabling the content rules. - However, only flexible (RegExp based) and configurable content filters are able to guard from any known and unknown yet unsafe internet content.
- Content Filters List
-
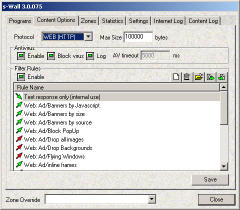 The dialog sets options for content filtering and antivirus options separately for each internet protocol. The product can process internet content before any other application and computer's storage. "Before" forces the application to wait while x-Wall will complete receiving and processing internet content. Each internet application has its own time limitation for waiting period. After that period expires, application will show an error. "MaxSize" avoids this problem. If an internet content size is below that value, x-Wall can fully process the content. If the size is above the content cannot be modified (It still can check viruses but cannot cure (block) them). The dialog sets options for content filtering and antivirus options separately for each internet protocol. The product can process internet content before any other application and computer's storage. "Before" forces the application to wait while x-Wall will complete receiving and processing internet content. Each internet application has its own time limitation for waiting period. After that period expires, application will show an error. "MaxSize" avoids this problem. If an internet content size is below that value, x-Wall can fully process the content. If the size is above the content cannot be modified (It still can check viruses but cannot cure (block) them).
The dialog contains the list of rules applied to current protocol. The rules may be  - enabled for outgoing traffic - enabled for outgoing traffic  - disabled for outgoing traffic - disabled for outgoing traffic  - enabled for incoming traffic - enabled for incoming traffic  - disabled for incoming traffic - disabled for incoming traffic- The rules can be edited, deleted and new rules may inserted with the toolbar, the right-mouse-button menu, or with the "Ins", "Del" and "Space" (for edit) keys. See Rules manual for the details.
- Inside Content Filtering
- The best place for the content filter is Windows network subsystem. That location of content filter provides application independence. All the applications make their network connection in the same way (using so-called TCP stack). It is the single place inside OS for providing network data to any Web browser, E-mail program, FTPs and other ones. Fortunately, the Windows developers foresee the well documented the network subsystem providing us the content filter compatible with all Windows versions.
- The Content filter works as follows. It can extract all the incoming\outgoing content directly from network subsystem for all the applications, detect the high-level protocol (HTTP, POP3 etc) without unnecessary settings and process each protocol separately with the internal engine (RegExp) or (theoretically) any external program, obtain engine results and put them transparently back to the network traffic.
|
 The dialog sets options for content filtering and antivirus options separately for each internet protocol. The product can process internet content before any other application and computer's storage. "Before" forces the application to wait while x-Wall will complete receiving and processing internet content. Each internet application has its own time limitation for waiting period. After that period expires, application will show an error. "MaxSize" avoids this problem. If an internet content size is below that value, x-Wall can fully process the content. If the size is above the content cannot be modified (It still can check viruses but cannot cure (block) them).
The dialog sets options for content filtering and antivirus options separately for each internet protocol. The product can process internet content before any other application and computer's storage. "Before" forces the application to wait while x-Wall will complete receiving and processing internet content. Each internet application has its own time limitation for waiting period. After that period expires, application will show an error. "MaxSize" avoids this problem. If an internet content size is below that value, x-Wall can fully process the content. If the size is above the content cannot be modified (It still can check viruses but cannot cure (block) them). - enabled for outgoing traffic
- enabled for outgoing traffic  - disabled for outgoing traffic
- disabled for outgoing traffic  - enabled for incoming traffic
- enabled for incoming traffic  - disabled for incoming traffic
- disabled for incoming traffic